The PDX (Product Data Exchange) delivery method is only available in OIEPs and is the recommended delivery method for use with PDX. STEP sends data to the PDX platform via the default PDX Outbound Integration Endpoint and the API.
Important: For environments using Product Data Exchange (PDX), configuration is required on your PDX system to implement AWS for asset delivery and/or AWS encryption. Contact Stibo Systems for information.
Note: Prior to Update 2025.2, this 'PDX' option was named 'Product Data Exchange 2' and the 'PDX (deprecated)' option was named 'Product Data Exchange'. The '(deprecated)' option is scheduled to be removed in a future update.
For additional information on PDX, refer to the Product Data Exchange topic within the Data Integration documentation, or contact Stibo Systems.
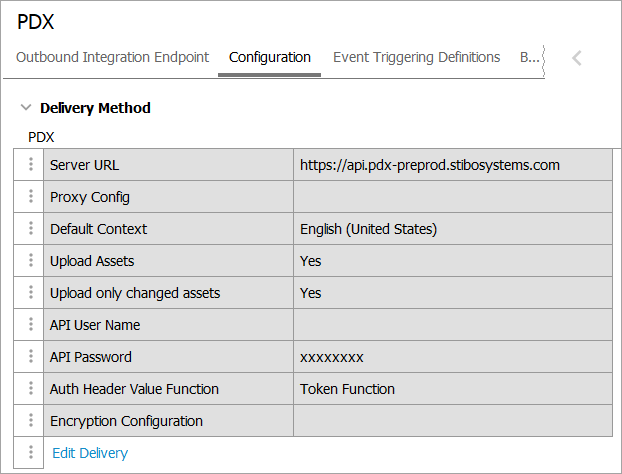
In an OIEP, the delivery method is displayed on the Configuration tab of the editor in the Delivery Method section.
Prerequisites
Note: The following functionality is managed by configuration properties that are not available in the Self-Service UI. Contact Stibo Systems Support for assistance.
The PDX.Url configuration property determines the PDX environments eligible in the OIEP configuration of the delivery method. Two PDX environments are relevant to this setting:
-
PDX Production (https://api.pdx.stibosystems.com)
-
PDX Pre-production (https://api.pdx-preprod.stibosystems.com)
General setup will include one account on the Production environment, which processes and syndicates live data, while multiple non-production accounts / clients may exist on the Pre-production environment. In the image below, STEP environments are in the column on the left, and those on the right represent PDX environments with PDX accounts.
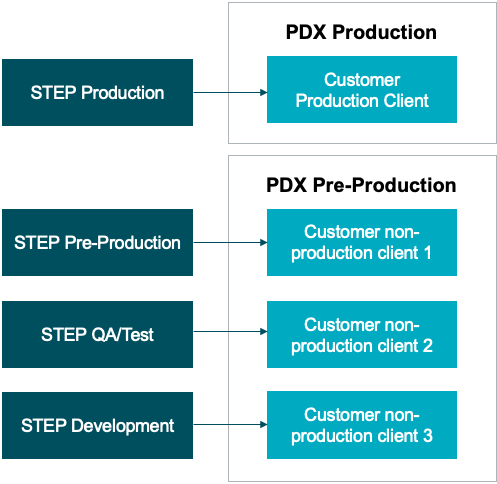
The properties required for the STEP Production environment specify the PDX Production environment (containing the customer’s production account / client) as the valid target of the PDX OIEP configured. If necessary, submit a ticket to the Stibo Systems Service Portal requesting to populate the PDX.Url property.
To ensure product information maintained in all the contexts selected for syndication in the PDX OIEP setup can be transferred, submit a ticket to the Stibo Systems Service Portal requesting to set the PDXDelivery2.LocaleChecking property to ‘false’.
- Determine the API user name and password. This will be required on the Edit Delivery Configuration dialog.
- Perform additional configuration required in the OIEP as laid out in the Setting Up the PDX OIEP topic in the Data Integration documentation.
Encryption Setting Prerequisites
Amazon Web Services (AWS) Key Management Service (KMS) encryption is optionally available for both data and assets in a PDX integration.
All encryption functionality is defined by four dynamic properties. The [Dynamic] placeholder text in each property must be replaced with same literal text to identify the purpose of the encryption properties and to associate them with each other. The literal text is displayed in the 'Encryption Config' parameter on the GIEP configuration dialog and in the 'Encryption Configuration' parameter on the 'PDX' delivery method on an OIEP. If multiple encryption methods are required, use a set of properties with the same literal text, such as 'PDXEncryption1' and 'PDXEncryption2.' In these examples, 'Dynamic' is replaced with 'PDXEncryption' literal text.
-
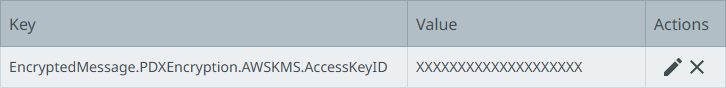
Configure the AccessKeyID using the EncryptedMessage.Dynamic.AWSKMS.AccessKeyID property.
-
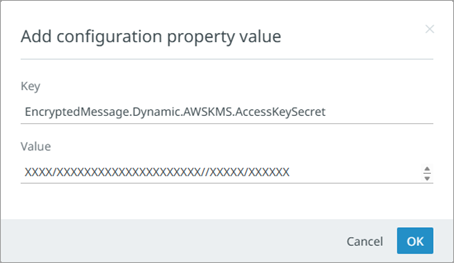
Configure the AccessKeySecret using the EncryptedMessage.Dynamic.AWSKMS.AccessKeySecret property. The access key secret is hidden.
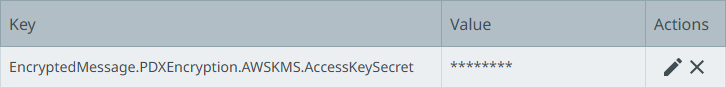
On the 'Add configuration property value' dialog, the Value field includes the access key secret.
-
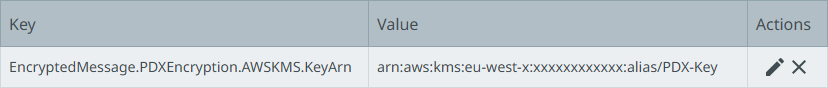
Configure the KeyArn using the EncryptedMessage.Dynamic.AWSKMS.KeyArn property.
-
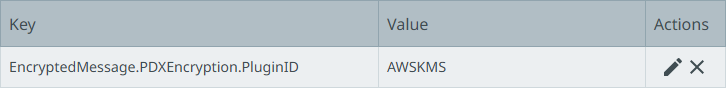
Configure the PluginID using the EncryptedMessage.Dynamic.AWSKMS.PluginID property with the value AWSKMS.
Important: AWSKMS is the only valid value for the PluginID property. Setting this required property associates it with the other properties that share the same dynamic value.
-
Proxy config parameter: Proxy functionality is intended for facilitating internet access, which is always available from SaaS environments. If a proxy is necessary for your scenario, contact Stibo Systems Support.
Configuration
For information on a parameter, hover over the parameter field to display help text.
-
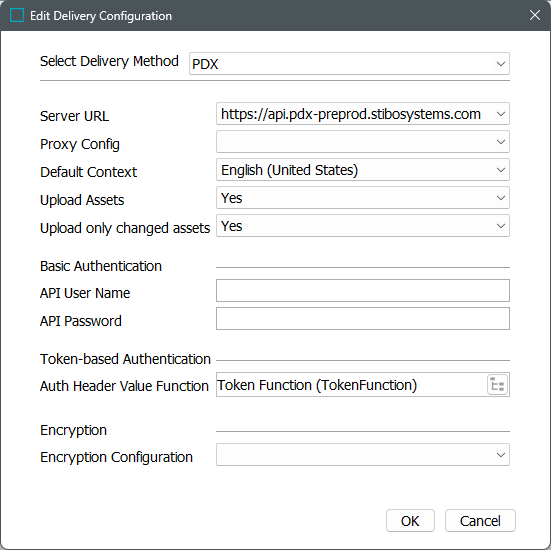
On the Configuration tab of the OIEP, in the Delivery Method section, click the Edit Delivery link to display the 'Edit Delivery Configuration' dialog.
-
For the Select Delivery Method parameter, choose PDX.
The following parameters are valid for all authentication methods.
-
Server URL - Select the appropriate target PDX environment.
-
Proxy Config - Proxy functionality is intended for facilitating internet access, which is always available from SaaS environments. If a proxy is necessary for your scenario, contact Stibo Systems Support.
-
Default Context - Specify which of the contexts included in the OIEP configuration is the default. The data in this context is used to populate the default language layer in PDX. The STEP Name in this default context will be the name of the master data product in PDX since the STEP Name in PDX does not have language layers.
Important: Channel assignment rules in PDX are evaluated based on the values available in the default language layer.
-
Upload Assets - determine the appropriate setting based on how you transfer assets to PDX.
-
Set to 'Yes' to send assets by the delivery method. 'Yes' is not allowed when using encryption (defined below).
-
Set to 'No' to exclude asset binary content, while still sending asset metadata. 'No' is required to use encryption (defined below).
-
-
Upload only changed assets - This parameter is only effective when the Upload Assets parameter is set to 'Yes'.
-
Set to 'Yes' to only include referenced asset objects where either the attribute values or the asset content has changed.
-
Set to 'No' to upload all existing assets.
-
-
The Basic Authentication section is required for API access via user name and password:
-
API User Name - Enter the API user name of a PDX user associated with a relevant account on the targeted environment.
-
API Password - Enter the API password of a PDX user associated with a relevant account on the targeted environment.
-
-
The Token-based Authentication section is required for token access via OAuth 2.0 authorization protocol:
-
Auth Header Value Function - Select a business function that produces the required authentication headers. For general information about business functions, refer to the Business Functions topic in the Business Rules documentation. For examples using basic authentication, refer to the Token-based Authentication Function Example section below.
-
-
The Encryption section is required for encrypting data (not assets) output to PDX.
Important: The 'Upload Assets' parameter (above) must be set to 'No' when encryption is used on this delivery method. If encryption is required for assets, use the Asset Publisher as defined in the Digital Assets documentation.
-
Encryption Configuration - If necessary, select an encryption option from those defined in the Encryption Setting Prerequisites section above.
-
-
Click the OK button to save the delivery method.
Token-based Authentication Function Example
Use the steps below to create an example business function for token-based authentication with or without using a proxy. (Proxy functionality is intended for facilitating internet access, which is always available from SaaS environments. If a proxy is necessary for your scenario, contact Stibo Systems Support.)
-
In PDX, go to Manage team / User management / API keys and generate a key. Refer to PDX Help Center / Documentation for more information.
Important: Existing PDX integrations moving to OAuth must not enter a source system ID when creating keys (which causes duplication of attribution created in the previous integration setup).
-
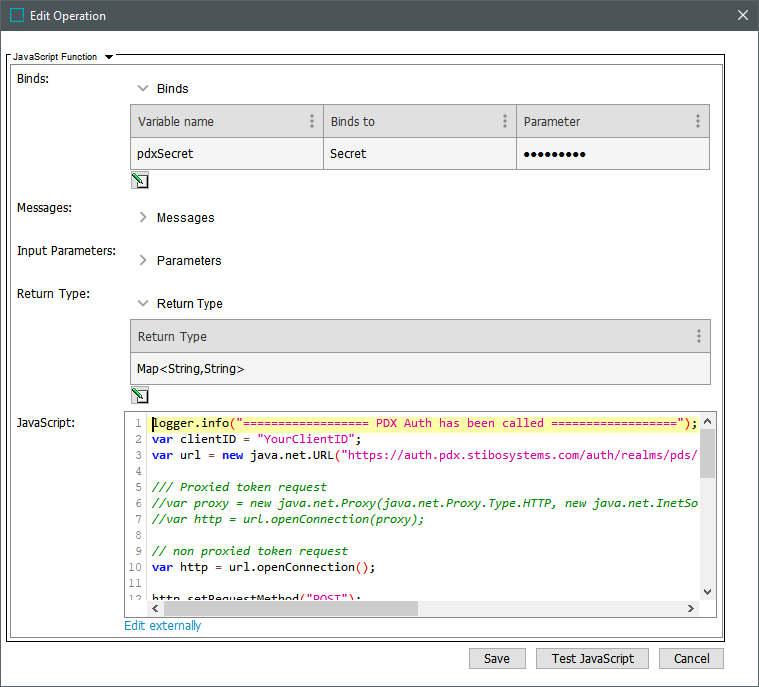
In STEP, create a JavaScript Function with:
-
Bind for secret (add variable name; Binds to = Secret; Parameter = ClientSecret (generated via PDX 'API keys' option)
-
Return Type = 'Map<String,String>'
-
JavaScript = example code below
-
-
Make necessary updates in the JavaScript for your system:
-
YourClientID = 'ID' of the generated API key
-
Verify the URL variable is aligned with the appropriate PDX environment (QA or PROD)
-
Proxy functionality is intended for facilitating internet access, which is always available from SaaS environments. If a proxy is necessary for your scenario, contact Stibo Systems Support. To use a proxy, uncomment the 'Proxied token request' section and modify as required.
-
Add your secret Bind variable (pdxSecret is used in this example)
-
-
Test your integration.
logger.info("================== PDX Auth has been called ==================");
var clientID = "YourClientID";
var url = new java.net.URL("https://auth.pdx.stibosystems.com/auth/realms/pds/protocol/openid-connect/token");
/// Proxied token request
//var proxy = new java.net.Proxy(java.net.Proxy.Type.HTTP, new java.net.InetSocketAddress(java.net.InetAddress.getByName("proxy.host.name"), proxyPortNumber));
//var http = url.openConnection(proxy);
// non proxied token request
var http = url.openConnection();
http.setRequestMethod("POST");
http.setDoOutput(true);
http.setRequestProperty("Content-Type", "application/x-www-form-urlencoded; charset=UTF-8");
http.connect();
var os = http.getOutputStream()
try {
os.write(new java.lang.String("grant_type=client_credentials&client_id="+clientID+"&client_secret="+pdxSecret).getBytes());
} finally {
os.close();
}
var input= http.getInputStream();
try {
var reader = new java.io.BufferedReader(new java.io.InputStreamReader(input));
var string ="";
while (reader.ready()){
string=string+reader.readLine();
}
var json = JSON.parse(string)
var map = new java.util.HashMap();
map.put("Authorization",json.token_type + " " + json.access_token);
logger.info("Authorization "+json.token_type + " " + json.access_token);
return map;
} finally {
reader.close();
}